Web Application Firewalls (WAFs) have become an essential part of IT security, especially in 2024, as they provide crucial protection for web applications and APIs. Let’s delve into understanding what WAFs are and how to select the right one for your company.
What is WAF?
A Web Application Firewall (WAF) is a specialized type of firewall designed to safeguard web applications and APIs against various cyber threats. WAF operates by scrutinizing, filtering, and blocking harmful web traffic and application-layer attacks, such as Distributed Denial of Service (DDoS), SQL injection, and cross-site scripting (XSS). Functioning at Layer 7 of the OSI model, WAFs provide a critical defense layer, allowing legitimate traffic to pass while identifying and stopping malicious requests. This nuanced approach ensures that web applications can safely interact with the internet, providing essential security for both businesses and their customers.
Understanding WAFs
Functionality: WAFs protect web applications by filtering, monitoring, and blocking malicious web traffic and application-layer attacks, such as DDoS, SQL injection, and cross-site scripting (XSS).
Evolution: Originating in the late 1990s, early WAFs protected against basic attacks like illegal character submissions. Modern WAFs have evolved to filter HTTP traffic, offering a more nuanced defense than traditional firewalls.
Approach: Rather than creating a barrier between internal and external networks, WAFs act as screens, allowing legitimate traffic while blocking harmful interactions.
Understanding The Similarities and Differences Between WAFs and NGFWs
Web Application Firewalls (WAFs) and Next-Generation Firewalls (NGFWs) are both integral components of network security but serve different purposes. The primary similarity lies in their objective to protect digital assets from cyber threats. Both types of firewalls analyze incoming traffic to prevent unauthorized access and attacks.
However, the key differences are in their scope and method of operation. WAFs are specifically designed to protect web applications by filtering HTTP traffic at the application layer (Layer 7). They focus on blocking attacks targeted at web applications, such as XSS and SQL injection. On the other hand, NGFWs combine the features of traditional network firewalls with additional capabilities, such as intrusion prevention systems and application awareness. NGFWs provide a broader range of network security by inspecting both network layer packets and application layer data, enabling them to block more varied types of unwanted traffic.
While WAFs are more specialized, protecting against common web application attacks, NGFWs provide a more holistic security approach, encompassing user-based policies and integrated threat intelligence. This distinction makes NGFWs versatile in capturing network traffic context, whereas WAFs are essential for securing internet-facing and cloud-native applications.
Choosing the Right WAF
Deployment Models: WAFs can be network-based, host-based, or cloud-based. The choice depends on where the web applications are hosted and the level of maintenance you’re willing to undertake. Network- and host-based WAFs require more setup and management, while cloud-based WAFs are simpler to deploy.
Blocklist vs. Allowlist: Blocklist WAFs block specific types of traffic or endpoints, while allowlist WAFs block all traffic by default, allowing only explicitly approved traffic. Many modern WAFs use a hybrid of these two models.
Integration with the IT Environment: WAFs should seamlessly fit into your existing architecture and be supported by your security operations team. Important considerations include in-line or tap/span placement, emerging architectural models like cloud and virtualization, and form factors.
Key Features to Consider
- API-Specific Threats: APIs are subject to unique security threats, including unauthorized data access, data manipulation, and service disruptions. An effective WAF should be equipped to identify and mitigate such threats.
- Complex Integration: Modern applications often integrate multiple APIs, increasing the complexity of the security landscape. A WAF with strong API protection capabilities can offer more comprehensive security.
- Custom Rule Setting: APIs might require custom security rules due to their specific structures and usage patterns. A WAF that allows for the customization of rules and policies for API traffic can provide more tailored and effective protection.
- Support for RESTful and SOAP APIs: With different types of APIs in use, such as RESTful and SOAP, it’s essential for a WAF to support various API protocols and be able to inspect and secure the traffic accordingly.
- Scalability and Performance: As APIs can handle large volumes of requests, the WAF should be able to secure APIs without impacting their performance and scalability.
- Compliance and Data Protection: APIs often handle sensitive data, making compliance with data protection regulations crucial. A WAF with robust API protection can help ensure compliance with standards like GDPR and HIPAA.
- Future of Web App and API Security (WAAS)
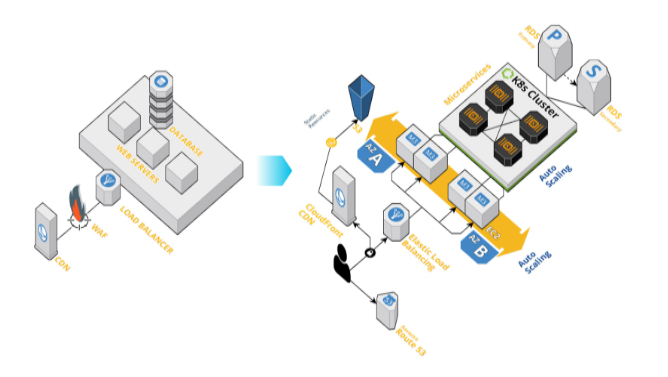
Shift from monolithic application to modern cloud-native application





